Conquering Cybersecurity
The challenges of maintaining cybersecurity—from securing personal computers to protecting government, military, financial, medical, and corporate systems from malicious attacks and unauthorized access—are ever evolving. In July, thousands of e-mails from Democratic National Committee employees were hacked and, soon after, released by WikiLeaks. The damaging aftermath revealed controversial information tied to the U.S. presidential campaign and also resulted in the resignation of the DNC chair. It is no secret that hackers are becoming smarter and more sophisticated, always on the lookout for new attack surfaces and vulnerabilities.
The DNC e-mail hack is just one of several high-profile cyberattacks of late; large companies have been affected by data breaches in recent years, and, as a result, millions of people’s personal data—from credit card and Social Security numbers to sensitive health information—have been compromised. Worldwide spending on cybersecurity initiatives reached $75 billion in 2015 and is expected to rise dramatically in the coming years.
For a system to be truly secure, everything in that system must be safeguarded—the hardware, the software, the router, the computer’s configuration, and the users’ access to the system.
Computer scientists at the Engineering School are working to fend off breaches and attacks, and, here, two professors tackle that with two distinct approaches—one focused on software security and the other on preventing hardware hacks.
Streamlining Software Security Processes
“To err is human . . .” the famous quote begins. And that is the crux of software security issues. Error-prone humans design and implement the software that is ubiquitous in homes, industry, and government, necessitating a focused effort to quickly and efficiently identify flaws in its design.
“By exploiting software bugs, attackers can gain control of software and the devices controlled by it, as well as steal privileged information,” says Junfeng Yang, associate professor of computer science and codirector of the Software Systems Lab.
Software security presents an interesting engineering challenge, chiefly because software engineering is a human activity based on fallible human problem-solving skills. It’s that fallibility that is responsible for security gaps in technology like smartphones, computers, and printers that we use for common, daily tasks. It also puts large-scale and complex technology—like medical equipment, drones, power grids, and space technology—at risk.
“For now, the creation and administration of program logic requires human intelligence, so we’ll be stuck with software systems written and administered by humans for a long time. That means we will have systems that are not 100 percent secure,” says Yang.
Is it possible to efficiently and effectively compensate for the human factor that results in software security issues? Yang thinks so.

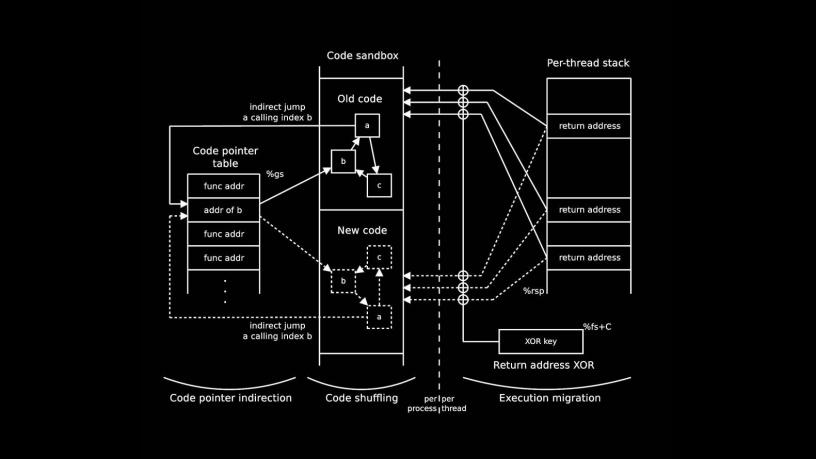
Fast and Deployable Continuous Code Re-Randomization Shuffler: Overview of shuffled code at runtime, as Shuffler executes a shuffle pass. The old code is shown with solid lines and the new code with dotted lines.
“My goal at Columbia Engineering is to build ‘self-driving’ technology for software engineering. I believe we can build intelligent tools to help detect and fix a lot of programming or admin errors, in order to increase reliability and security,” he explains. “The concept is similar to self-driving cars in which we program a destination and the car drives autonomously, safely navigates streets and highways, and gets us where we want to go.”
Yang is already making headway toward that goal. One of his earliest innovations tackled the problem of storage system errors in crash-recovery code. He employed an automatic verification technique called model checking to develop eXplode, a solution that makes it easy to find such bugs, even on complex storage stacks built from many different subsystems. Similarly, his team also examined the reliability problems inherent in multithreaded software programs commonly used in web servers. Testing, analyzing, and verifying multithreaded programs is notoriously difficult, leading to a greater probability for undiscovered bugs that can be exploited by attackers. His StableMT solution improves the analysis and testing of these programs and enhances reliability.
“It requires a lot of manual effort to detect bugs, so it would be great if we could automate much of this process using software to scan software,” he remarks. “We report potential bugs to the developers, and they create patches to their own software.”
Collaboration is key to identifying and solving the unique security and reliability challenges inherent in the multitude of software programs constantly in development. Along with his PhD student Younghoon Jeon, Yang has developed an automated solution to diagnose performance slowdowns in mobile apps. He’s also working with Yinzhi Cao at Lehigh University on machine unlearning—an automatic repair system that scrubs unwanted data injected in learning systems via malicious attacks or security breaches. Machine unlearning can also make learning systems forget users’ data for better privacy.
“There are many computer paradigms, and new ones on the horizon, each with potential security vulnerabilities,” he says. “The key to efficiently and effectively overcoming these security and reliability issues in both software and hardware is advanced computer science.”
A Firm Foundation for Security
In the world of cyberattacks, software is the lowhanging fruit that fraudsters typically exploit. But as software security becomes tighter, attackers are looking for opportunities to take advantage of weaknesses in hardware—the foundation for an entire computer stack. The prize is deeper control of systems and devices.
Computer scientists like Simha Sethumadhavan, associate professor of computer science and founder of the hardware security startup Chip Scan, are working hard to get ahead of these exploits and find fixes for this potential cybersecurity nightmare.
“Cybersecurity is a current, pressing problem, and the practical solutions can have a huge impact,” says Sethumadhavan. “With the world becoming so hyperconnected, cyberattacks can lead to cascading, catastrophic failures. Solving this problem is where Columbia Engineering really excels. We really understand what needs to be done.”
Focusing on the hardware part of the cybersecurity quotient is both art and science. “Perfect security is a fool’s errand in some sense, and the aim of the game is to raise the bar to make it harder for the attacker to exploit a vulnerability,” says Sethumadhavan. “There’s a lot of engineering involved.”

Sethumadhavan’s work takes a long-term, principled approach to mitigating risk. He advocates for a “hardware-up” security method to design systems with security as a first-order requirement. “Today security is layered on insecure foundations with unreasonable trust assumptions. A principled way to approach full-system security is to secure the hardware first against attacks, and then create security services rooted in the hardware that enable development of lean security software,” he explains. “This approach is a new way to engineer safe systems with full emphasis on the use of hardware to not only make security faster and more efficient but also to improve the effectiveness of security solutions by improving security of both hardware and software.”
To achieve hardware-up security, his group works on nullifying hardware “backdoors,” malicious pieces of code placed in hardware that can be hard to detect and impossible to remove.
“One type of hardware backdoor behaves like a ticking time bomb. One solution is to change attackers’ assumptions about hardware design, effectively elongating the fuse on these malicious pieces of code so the bomb never goes off,” says Sethumadhavan. His group’s solution is being evaluated by U.S. Air Force Labs to keep their supply chain safer.
Sethumadhavan’s lab has also found a way to make antivirus protection more effective and energy efficient. “The big engineering question was how to make antivirus protection better so that it could guard the device better but consume the lowest amount of energy possible,” he remarks.
The solution? Bake the antivirus into silicon. “This antivirus in silicon can’t be easily turned off and uses less energy even though it runs continuously to protect the system.” That work has gained commercial notice and has influenced development of new, highly secure consumer products.
“In a couple of years from now, it is very likely you will be able to purchase a smartphone with an antivirus system embedded in it that is easier on battery life,” says Sethumadhavan. “That’s inspired by our work.”